I installed and configured RSH on CentOS release 5.5 . The steps would be almost same for all the other linux distros.
First you need to have xinetd installed. For that fire the following command:-
user@centos# yum install xinetd
Once its installed, you need to install rsh-server onto your machine. For that enter the following command:-
user@centos# yum install rsh-server
Now you need to Edit /root/.rhosts to add lists of hosts that can access without password. If you want to allow access to everyone without password, you need to put '+' in the file. A '+' indicates allowing everyone.
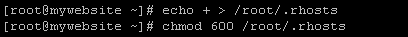
To do this, you can either modify the file by opening it or just enter the following command:-
user@centos# echo + > /root/.rhosts
Now you need to modify the permissions of .rhosts file. Enter the following command:-
user@centos# chmod 600 /root/.rhosts
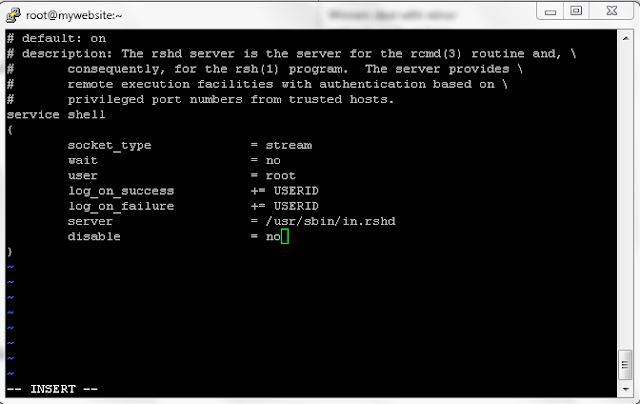
Now you need to allow RSH , RLogin and Rexec to be used. For that you need to modify the /etc/xinetd.d/rsh , /etc/xinetd.d/rlogin and /etc/xinetd.d/rexec file. Open these files one by one and then set the "disable=no"
Here is an example for modifying the rsh file:-
user@centos# vi /etc/xinetd.d/rsh
Similarly do for the rlogin and rexec file.
Once these are done, now you need to modify the /etc/pam.d/rsh file to allow passwordless rsh to the machine.
You need to modify the following line:-
First you need to have xinetd installed. For that fire the following command:-
user@centos# yum install xinetd
Once its installed, you need to install rsh-server onto your machine. For that enter the following command:-
user@centos# yum install rsh-server
Now you need to Edit /root/.rhosts to add lists of hosts that can access without password. If you want to allow access to everyone without password, you need to put '+' in the file. A '+' indicates allowing everyone.
To do this, you can either modify the file by opening it or just enter the following command:-
user@centos# echo + > /root/.rhosts
Now you need to modify the permissions of .rhosts file. Enter the following command:-
user@centos# chmod 600 /root/.rhosts
Now you need to allow RSH , RLogin and Rexec to be used. For that you need to modify the /etc/xinetd.d/rsh , /etc/xinetd.d/rlogin and /etc/xinetd.d/rexec file. Open these files one by one and then set the "disable=no"
Here is an example for modifying the rsh file:-
user@centos# vi /etc/xinetd.d/rsh
Similarly do for the rlogin and rexec file.
Once these are done, now you need to modify the /etc/pam.d/rsh file to allow passwordless rsh to the machine.
You need to modify the following line:-
BEFORE: auth required pam_rhosts_auth.so
AFTER : auth required pam_rhosts_auth.so promiscuousNow you are done. You need to restart the xinetd service.
user@centos# /etc/init.d/xinetd restart
Now run the rsh command with the other commands and you will be able to successfully
execute them.
If there are any warnings or errors as you are trying to access using the root
privileges, then you need to modify the /etc/securetty file. Add rsh and rlogin
to the bottom of that file.
Now you would be able to successfully perform rsh to the machine.




Thank you for the detailed and precise reference to setup rsh. Information here is difficult to find elsewhere.
ReplyDeleteTRADING SCAM ALERT
DeleteCrypro Trading, Forex Trading, Stock Trading and their likes are a means of making money but it’s more like gambling. There are no sure means to guarantee that a person could make profit with them and that’s why it can also be reasoned to be scam. Let’s not forget that some individuals even give you % guarantee of making profits and end up running away with your money.
You might have also come across some individuals that say they will give you guarantee on successful trades but they only end up as SCAMMERS as well. You here them say stuffs like 200% guaranteed in just 2 weeks and when you go into trade with them, they start telling you to pay profits percentage before you can get your income. These are all liars please avoid them. But if you have been a victim of this guys, then you should contact FIRMWARE now
The internet today is full of Recovery Scam, you see so much testimonies been shared about how a firm or Company helped them recover what they lost to this Trading, but believe it, it’s just a way to lure more people and end up scamming them.
The big Question is “Can someone Recover their money lost to Binary Option and Scam
I will say yes, and will tell you how.
The only way to Recovery your money back is by hiring HACKERS to help you break into the Firms Database Security System using the information you provide them with, Extract your file and get back your money. It seems like a really impossible thing to do, I will tell you, it should be impossible, but with the use of specially designed softwares known to HACKERS and Authorities (such as The FBI, CIA e.t.c) it is possible and the only way to recover your money.
FIRMWARE are a group of hackers who use their hacking skill to hunt down SCAMMERS and help individuals recovery their money from Internet SCAMMERS.
We just need the contact details of the SCAMMERS and Paymnet Info and within 4-8 hours your money will be return to you.
This are services we offer-:
Crypto scam money recovery
lost loan money recovery
money laundry recovery
Device hack
Bank issues
Access to school/company/fellowship/organization files
Lost cars tracking
fraud payment
Access to cheating husband/wife device
. Loextending and subtracting of stamped file concerning a giving end line period of time
tracing and recovering lost emails/ conversations/contacts / and accessories
ETC
You can contact us via the emails below-:
cyberhackingcompany@gmail.com
HACKERS ©️
2022 All right reserved ®️
Thank you. This was very well explained. Appreciate it.
ReplyDeletegreat man.....
ReplyDeleteReplyI basically think we all don't have to face all this deceit and lies from our spouse…in a case of mine when i got sick and tired of all the lies and deceit i had to contact a friend of mine to get me the contact of one of the best hackers in the states ..then i met cryptocyberhacker@gmail.com .He saved me from the lies of my cheating boyfriend by hacking his phone.. In case you need help with hacking any phone or account, Hack into any hack websites, Hack into any company website, Hack into any database system and grant your admin privilege, Hack pay-pal account, Hack word press blogs Server crashed hack or other jobs.. Contact cryptocyberhacker@gmail.com.Tell him i referred you.
ReplyDelete