Requirements:-
1. Gateway should have 2 nics, one to access internal network and other to access public network.
2. Internal machines should be connected via switch/hub to private nic of Gateway/Machine A.
In the setup mentioned below, I am using 2 VMs, config of each VM is as shown below:-
Config of Gateway:-
2 nics attached to VM.
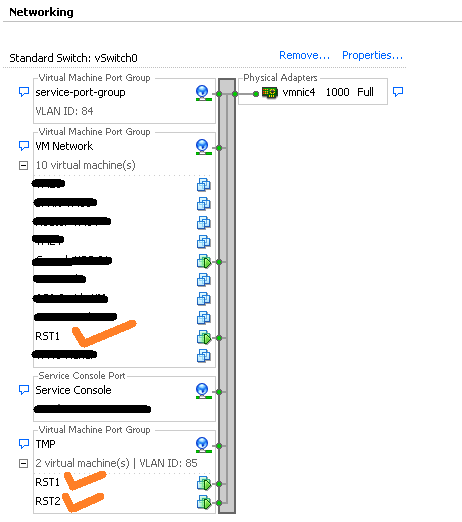
First nic attached port-group "VM Network" which can access the public network.
Second nic added port-group "TMP" which allows only VLAN 85 traffic. Hence its a private network.
Config of internal VM:-
Internal VM is having only 1 nic. This nic is assigned a port-group TMP such that its a part of private network and can access nic1 of Gateway VM.
Network setup for the above is as follows(Note that Gateway VM is named as RST1 and internal VM is named as RST2):-
Assign IP address to Nic1 on the Gateway machine which is a part of the private network.
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto eth0
iface eth0 inet dhcp
auto eth1
iface eth1 inet static
address 10.3.1.1
netmask 255.255.255.0 To enable routing functionality on Linux, one needs to enable IP forwarding. You can do the same by entering the following command:-
# echo “1″ > /proc/sys/net/ipv4/ip_forward
To make the changes persistent across reboots, just add the following line in "/etc/sysctl.conf". Open this file in your favourite editor and add the following line:-
net.ipv4.ip_forward = 1
Reboot your machine.
Now you need to add Gateway functionality to this VM. For this, you need to add IPTable rules such that traffic coming on nic1 is sent out through nic 0. You can enter the following commands on the Linux terminal:-
/sbin/iptables -P FORWARD ACCEPT
/sbin/iptables --table nat -A POSTROUTING -o eth0 -j MASQUERADE
You can also add the above two lines at the bottom of "/etc/rc.local" file so that changes are present even after reboot. Now your basic NAT gateway is up and running.
To test the functionality of the Gateway, just provide the gateway address as the address of eth1 of Gateway and you will be able to connect to the outside world using Gateway. Below mentioned is the "/etc/network/interfaces" file of inside VM.
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto eth0
iface eth0 inet static
address 10.3.1.2
netmask 255.255.255.0
gateway 10.3.1.1
Now if you will try to ping to outside world using this internal VM, you would be able to do so using the gateway.
Somethings you can try:-
Try configuring the Gateway such that you can SSH to the VMs behind the Gateway. You need to enable Port-Forwarding for the same. Happy configuring. :)
Last but not the least, I would like to thank my special friend for coming up with the idea to learn together and do this setup. Hopefully we both would do a lot more funny experiments in future. Thanks again to that friend. :)


Need The To Hire A Hacker❓ Then contact PYTHONAX✅
ReplyDeleteThe really amazing deal about contacting PYTHONAX is that the Hack done by us can’t get traced to you, as every Hacking job we do is strongly protected by our Firewall. It’s like saying if anyone tries to trace the Hack, it will lead them to us and we block whatever actions they are doing.
We have been Invisible to Authorities for almost a decade now and if you google PYTHONAX, not really about us comes out, you can only see comments made by us or about us.
Another Amazing thing to you benefit from Hiring our Hackers is that you get a Legit and the best Hacking service, As we provide you with Professional Hackers who have their Hacking Areas of specialization.
We perform every Hack there is, using special Hacking tools we get from the dark web.
Some list of Hacking Services we provide are-:
▪️Phone Hacking & Cloning ✅
▪️Computer Hacking ✅
▪️Emails & Social Media Account Hacking✅
▪️Recovering Deleted Files✅
▪️Tracking & Finding People ✅
▪️Hunting Down Scammers✅
▪️Hack detecting ✅
▪️Stealing/Copying Files & Documents From Restricted Networks and Servers ✅
OTHER SPECIAL HACKING SERVICES
▪️Binary Option Recovery ✅
▪️Scam Money Recovery✅
▪️Bitcoin Multiplication✅
▪️Change Of Grades In Universities/Colleges ✅
▪️Phone Calls Monitoring✅
▪️keyLogging Installation✅
▪️Remote Access Trojan (RAT) installation ✅
▪️Cyber Security Upgrade✅
▪️And lots more...........
Whatever Hacking service you require, just give us an Email using the Emails Address provided below.
pythonaxhacks@gmail.com
pythonaxservices@gmail.com
PYTHONAX.
2020 © All Right Reserved.